In one of the most significant cybersecurity incidents of 2025, the Russia-linked Everest ransomware group has claimed responsibility for stealing over 1.5 million passenger records connected to Dublin Airport. The breach, which reportedly originated from a third-party supplier, has raised serious concerns about data security within the European aviation sector. The exposed data allegedly stems from Collins Aerospace’s MUSE check-in platform — a shared system used across multiple airports and airlines. The Dublin Airport Authority (daa) confirmed that a supplier-related cyber incident occurred and that investigations are ongoing with the Irish Data Protection Commission and affected partners. This incident marks one of the largest aviation-related data exposures in Europe to date and highlights the growing risks associated with supply-chain vulnerabilities in critical infrastructure.
Technical Details of the Attack
The Everest group reportedly gained access through an exposed file transfer protocol (FTP) server using outdated credentials at Collins Aerospace, a subsidiary of RTX Corporation. From this entry point, the attackers moved laterally through the network, eventually infiltrating production environments tied to airport operations data. This breach caused temporary disruptions in check-in systems across several major European airports, including Heathrow in the UK, Brussels in Belgium, and Berlin Brandenburg in Germany.
The affected airports were forced to revert to manual check-in procedures, resulting in widespread delays. The attack targeted the MUSE platform — a multi-tenant check-in and passenger management system servicing numerous European airlines — emphasizing the inherent risks of shared IT infrastructure within aviation networks. Analysis of the stolen dataset indicates that the compromised data originated from a vendor-level environment rather than directly from Dublin Airport, suggesting that multiple airports may have been indirectly affected.
Scope and Nature of the Data Theft
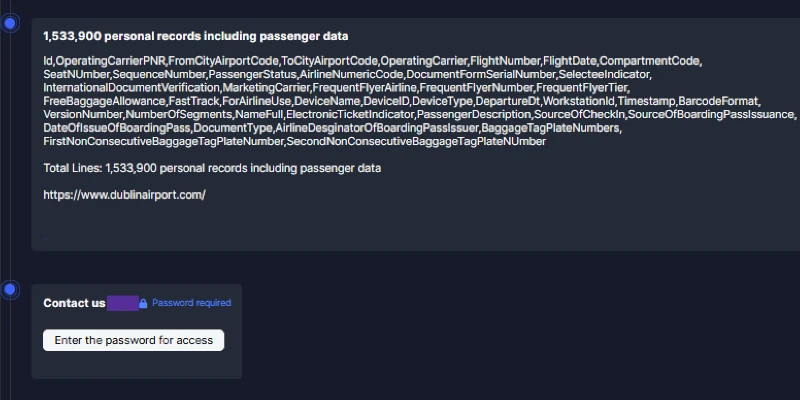
The Everest group claims to have exfiltrated 1,533,900 passenger records containing a broad range of sensitive information. The stolen data reportedly includes personal identifiers such as full names, frequent flyer details, and membership numbers, alongside extensive travel-related information including flight numbers, booking references, seat assignments, and ticketing data. Records also contained metadata such as baggage tag numbers, boarding pass details, document verification statuses, and timestamps from check-in terminals. Technical identifiers such as device names, workstation IDs, and software version numbers were also among the exposed data, suggesting that the attackers accessed operational-level systems with considerable depth. The detailed nature of this dataset heightens the potential for identity theft, phishing campaigns, and fraudulent travel-related schemes targeting affected passengers.
Ransom Demands and Threat Actor Activity
Following the breach, the Everest ransomware group listed both Dublin Airport and Air Arabia on its dark-web victim portal. Each listing was password-protected, indicating that negotiations or ransom discussions were likely underway. The group reportedly set countdown timers of five to six days, threatening to release the stolen data publicly if the victims did not respond or comply with payment demands. While the authenticity of the dataset has not been independently verified, the specificity and structure of the alleged passenger information lend credibility to Everest’s claims. The daa confirmed that the incident involved a third-party supplier and emphasized that no daa internal systems were directly compromised, aligning with the ransomware group’s narrative of a vendor-based breach.
The Everest Ransomware Group
Emerging in mid-2021, the Everest group has become a prominent player in the cyber extortion landscape, frequently associated with Russian cybercrime networks and possibly linked to the BlackByte ransomware operation. Everest is known for its “double extortion” tactics, where attackers not only steal sensitive data but also threaten to publish it if ransom demands are not met. The group’s victim list spans multiple industries and regions, including BMW, Coca-Cola Europacific Partners, DZ Bank, and various government and healthcare entities across the Middle East and Europe. In September 2025, Everest was also linked to a cyberattack against Collins Aerospace, the same vendor implicated in the Dublin Airport breach. This pattern suggests an increasing strategic focus on aviation, logistics, and critical infrastructure — sectors where disruption carries immense operational and reputational consequences.
Investigation and Regulatory Response
Dublin Airport Authority swiftly launched an investigation in coordination with the Irish Data Protection Commission and affected airlines. The daa confirmed that the cyber incident stemmed from Collins Aerospace’s systems and that it was working closely with regulators to assess the impact on passengers. Travelers who flew through Dublin Airport between August 1 and August 31, 2025, were advised to remain vigilant for suspicious activity related to their travel accounts. Collins Aerospace has not issued a detailed statement about the claimed data theft but previously described a “cyber-related event” affecting its systems. Independent cybersecurity researchers have since corroborated that a ransomware intrusion exploiting an unsecured FTP interface was the likely cause. The breach has also attracted attention under the EU’s NIS2 Directive, which could trigger a broader review of cybersecurity compliance among aviation technology vendors and service providers across Europe.
Risks and Industry Implications
The exposure of over 1.5 million detailed passenger records poses serious risks to both individuals and organizations. For passengers, the compromised data increases vulnerability to identity theft, phishing scams, and fraudulent travel notifications. The inclusion of highly specific information such as seat numbers, flight dates, and baggage tags enables attackers to craft highly convincing impersonation schemes. For airlines and airports, the breach underscores the dangers of centralized IT dependencies, revealing how a single supplier compromise can ripple across multiple operations. Reputational damage, regulatory penalties under GDPR, and long-term trust erosion represent significant consequences. Industry experts warn that shared platforms like MUSE — while operationally efficient — introduce complex security risks that demand enhanced oversight and segmentation. The event serves as a stark reminder that supply-chain security has become a critical front line in aviation cybersecurity.
Broader Cyber Context
Cybersecurity analysts observing the incident note a clear shift in Everest’s operational strategy toward data exfiltration and monetization rather than pure ransomware encryption. This mirrors a wider trend in the global threat landscape, where cybercriminals target high-value data for extortion rather than system paralysis. The Dublin Airport breach illustrates how interconnected systems within aviation can lead to cascading effects across borders. The attack also reinforces the growing importance of implementing zero-trust architectures, stronger vendor security audits, and real-time dark web monitoring for early leak detection. As Everest continues its campaign against critical European sectors, including transport and aerospace, cybersecurity resilience is increasingly viewed as essential national infrastructure protection.
Mitigation and Preventive Measures
Experts recommend that affected passengers monitor loyalty programs, airline accounts, and booking systems for unusual activity. Suspicious messages referencing flight details should be treated with extreme caution, as threat actors may exploit stolen data to launch targeted phishing campaigns. Organizations across the aviation ecosystem are urged to strengthen vendor management practices, enforce multi-factor authentication, and conduct regular penetration testing of shared platforms. Maintaining offline backups and adhering to GDPR and NIS2 incident reporting requirements remain key components of effective incident response. Beyond immediate containment, this breach underscores the need for systemic cybersecurity reforms across the aviation supply chain.
Conclusion
The Everest ransomware attack on Dublin Airport represents a watershed moment for aviation cybersecurity, exposing the fragility of shared systems and third-party dependencies. While the daa and its partners work to assess and mitigate the damage, the incident serves as a stark reminder that modern airports are as much digital ecosystems as physical hubs. As cybercriminal groups evolve toward data-centric extortion, safeguarding the personal and operational data of millions of travelers has become a core component of aviation safety. Strengthening vendor oversight, enforcing zero-trust principles, and building resilience against supply-chain threats will be vital in protecting the future of global air travel.
























0 Comments