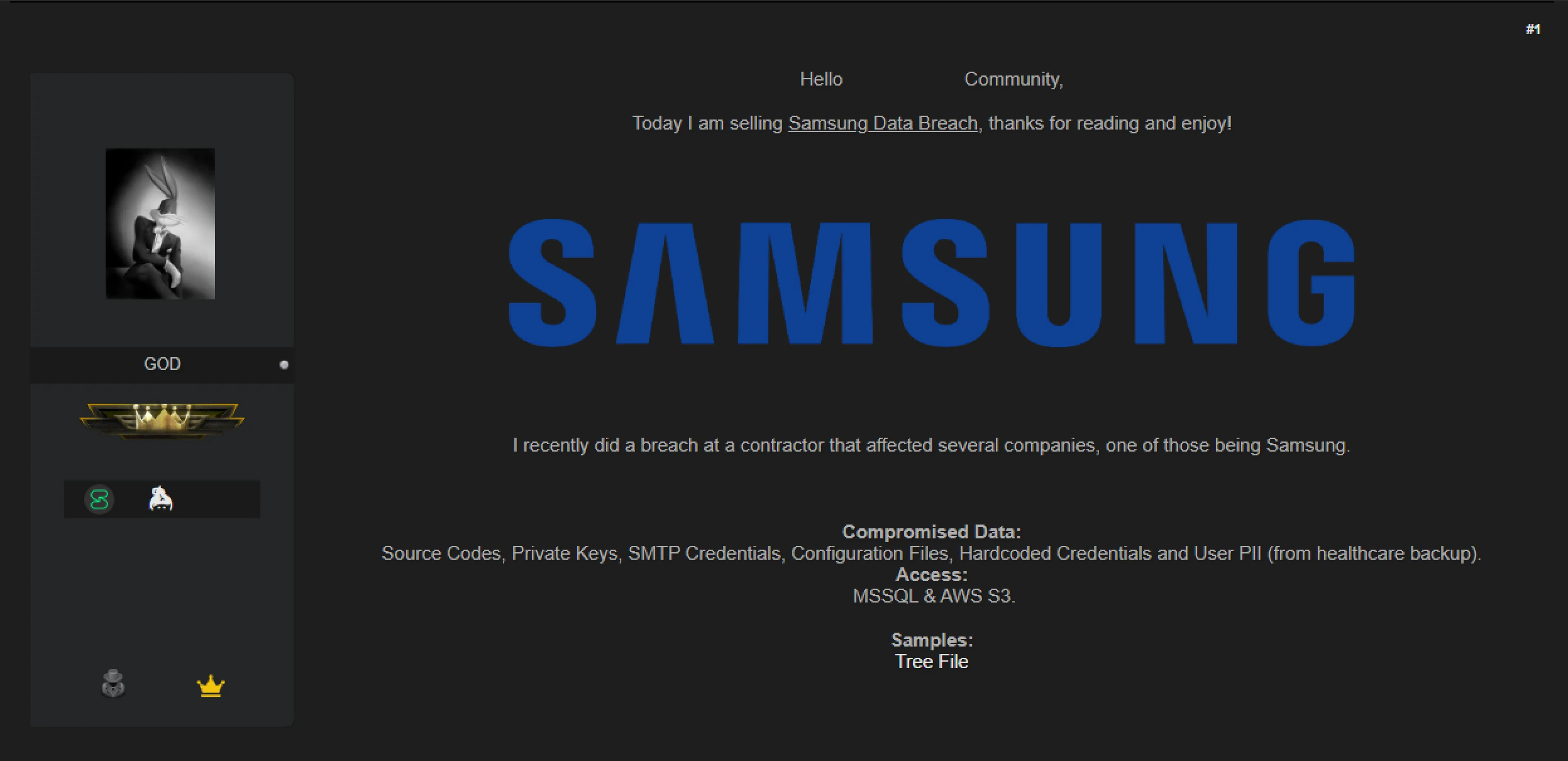
According to reports, a hacker known as "888" has claimed responsibility for a breach involving Samsung Medison, a subsidiary of Samsung Electronics. The hacker asserts that they accessed sensitive internal data through a vulnerability in a third-party contractor’s system. The breach reportedly exposes a significant amount of confidential data, including source code, private keys, and personally identifiable information (PII) associated with healthcare systems. While this breach does not directly involve Samsung Electronics, the breach of Samsung Medison, which operates under its own corporate structure, is still cause for concern due to the sensitive nature of the stolen data.
What Was Exposed
According to the hacker’s post, the stolen data includes source code, private keys, SMTP credentials, configuration files, hardcoded credentials, and user PII. These types of data are critical to the operations of Samsung Medison, as they support both internal software systems and the infrastructure behind medical equipment. In particular, the exposure of private keys and hardcoded credentials could allow malicious actors to gain unauthorized access to critical systems, potentially compromising the integrity of the equipment and services Samsung Medison provides to healthcare environments.
Researchers have also analyzed data samples posted by the hacker, which show what appears to be internal project files, likely linked to Samsung Medison’s proprietary software. These files suggest that the breach included the theft of important source code and configuration files. While hardcoded credentials were not explicitly provided in the hacker’s post, the presence of other sensitive data implies that such credentials may have been compromised, further raising the risk of unauthorized access to corporate systems.
Additionally, screenshots of stolen databases revealed employee contact information, including emails and usernames. While it is unclear how these usernames are used, they may be tied to internal systems or administrative access. Exposing these details could lead to social engineering attacks or credential stuffing, where attackers attempt to use the stolen information to gain unauthorized access to other accounts.
Privacy Risks and Security Concerns
The breach of Samsung Medison’s systems has significant implications for privacy, especially in the healthcare sector. Samsung Medison is involved in developing medical equipment and technologies that are used within healthcare environments, meaning the compromised data could include sensitive information related to patients or healthcare providers. The hacker claims that some of the exposed data includes backup files from healthcare systems, further amplifying the breach’s potential consequences.
Given the nature of the stolen information, the breach could lead to privacy violations for individuals whose data is included in the exposed records. The PII that has been stolen could be used to target employees or customers for phishing attacks, social engineering schemes, or identity theft. Furthermore, the exposure of source code and system credentials could allow attackers to exploit vulnerabilities in Samsung Medison’s medical devices or software platforms, potentially leading to system disruptions or manipulation of equipment.
Third-Party Contractor Vulnerabilities
The breach also highlights a broader and increasingly dangerous cybersecurity trend: the exploitation of third-party contractor vulnerabilities. As organizations expand their operations and rely on external vendors for specialized services, they inadvertently expose themselves to the risks posed by these third parties. In this case, the hacker claims that the breach occurred due to the compromised access of a contractor, not directly through Samsung Medison’s systems. This method of attack has become more common in recent years, as cybercriminals increasingly target the weaker links in the supply chain to gain access to larger, more secure networks.
The risks posed by third-party contractors are significant, especially when these external vendors are given access to sensitive data or internal systems. Companies may have robust internal cybersecurity defenses in place, but if a third-party contractor is not adequately protected, it can serve as an entry point for attackers. This type of breach is not unique to Samsung Medison—similar attacks have targeted major organizations worldwide, exploiting vulnerabilities in their third-party supply chains.
Conclusion
While this breach is specifically tied to Samsung Medison, it reflects a larger trend in cybersecurity where third-party contractor vulnerabilities are increasingly exploited by cybercriminals. For Samsung Medison, the immediate concern is the exposure of sensitive healthcare data and the potential for further exploitation of system credentials. It remains to be seen how Samsung Medison will respond to the breach, but the company’s handling of the situation will have significant consequences for its reputation in the healthcare industry.
























0 Comments