Despite the security measures in place on dark-net markets, there are occasions where both markets and users inadvertently make errors that may expose them to law enforcement. Operational security lapses, such as using identifiable information or unencrypted communications, or technical vulnerabilities within the market itself, can result in breaches of anonymity. Even highly secure systems can fail when users are not vigilant. These occasional mistakes have led to high-profile investigations, where law enforcement has been able to identify vulnerabilities and exploit them.
Real-world examples, such as the takedown of Silk Road in 2013, illustrate how small operational oversights—like the use of identifiable usernames—can lead to the identification of users and subsequent prosecution.
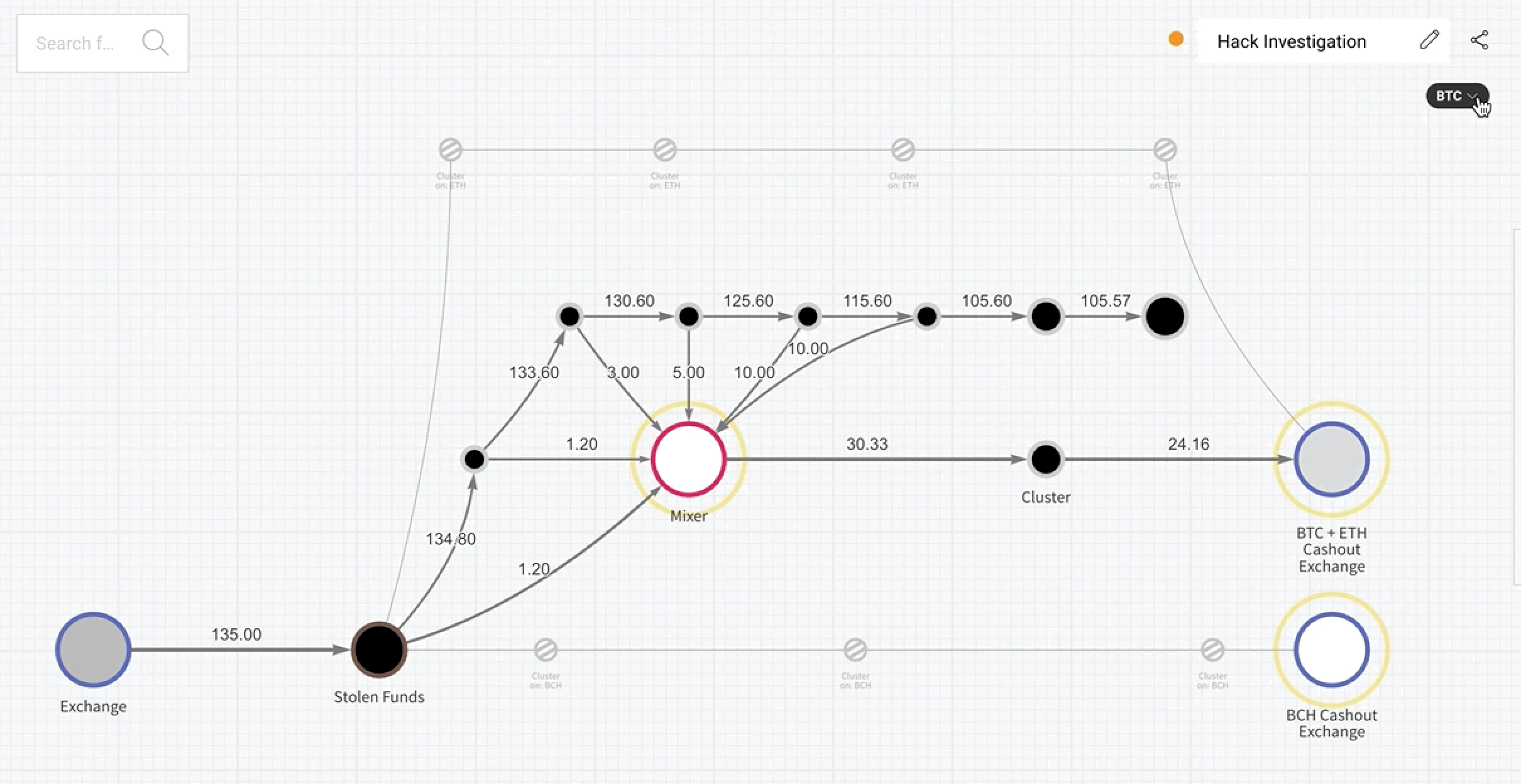
Cryptocurrency Tracking
Cryptocurrencies on dark-net markets vary from transparent ledgers, like Bitcoin and Ethereum, to privacy-enhancing coins designed to make tracking transfers more difficult. Mixers and tumblers can complicate on-chain tracing, while privacy coins like Monero use advanced cryptographic techniques to minimize visible linkability. However, these tools are not immune to investigation: when a mixer or its operators are seized, law enforcement has sometimes recovered metadata or other records that can reconnect mixed deposits and withdrawals. Centralized exchanges, which follow Know Your Customer (KYC) regulations, can also convert otherwise anonymous transactions into real-world identities.
When a market is seized, it can provide investigators with critical data, such as servers, databases, escrow wallets, private keys, and archived messages. These resources help authorities connect accounts, transactions, and communications. Even when privacy coins are used, forensic analysis, combined with network-level data or other investigative leads, can provide valuable insights. While privacy measures like mixers and privacy coins increase the complexity of tracing funds, they do not guarantee complete anonymity.
For example, in the 2017 takedown of the AlphaBay Market, law enforcement was able to trace users' cryptocurrency transactions despite the use of privacy-enhancing tools, ultimately seizing over $23 million in cryptocurrency.
Surveillance and Monitoring
Law enforcement utilizes multiple techniques to deanonymize Tor users. Investigations often involve a combination of network-level correlation, server-side compromise, browser signals, and traditional forensics. For instance, network correlation can link observed traffic flows to a Tor circuit when both ends are visible to adversaries. Traffic-shaping and website fingerprinting further assist in matching packet size and timing patterns.
Server compromises or court-authorized web exploits have been used to directly identify IP addresses or host information by targeting vulnerable clients or servers. Large-scale takedowns often provide substantial evidence—such as seized servers and database dumps—that can turn technical leads into actionable cases.
At the client layer, Tor Browser helps mitigate common fingerprinting risks by standardizing responses and blocking or limiting the use of plugins. However, vulnerabilities in non-default clients, modified settings, or external extensions can sometimes expose users. Strict security measures, like disabling JavaScript and using Tor's highest security settings, are critical to reducing the risk of exploitation. JavaScript, in particular, is one of the most common attack vectors used to deanonymize users, and disabling it prevents malicious scripts from leaking identifying information.
Despite the anonymity provided by Tor, operational mistakes like reusing identifiers, failing to anonymize external communications, or linking accounts on KYC-enforced exchanges can create significant risks. Additionally, recent changes in Tor, such as the removal of user-agent spoofing, have sparked controversy, as this feature used to allow users to mask their operating systems, further protecting against browser fingerprinting. These investigative techniques are probabilistic and require specialized capabilities, often enhanced by cross-channel methods like financial tracing.
Data Analysis and Machine Learning
Authorities also employ AI and data-analysis techniques to track Tor traffic. By identifying patterns in signals like posting times, writing styles, transaction timings, wallet reuse, and account migrations, investigators can create connections to specific Tor traffic flows. This can be further supported by network metadata from logs of Tor relays, ISPs, VPNs, or seized servers.
While AI plays a role in flagging potential links, these findings often require further corroboration through traditional investigative methods, such as server seizures and financial tracing. Legal access to logs or physical evidence is frequently needed to confirm these correlations. Though routing traffic through VPNs or other intermediaries can obscure the source of Tor traffic, such measures still depend on the visibility available to investigators and the lawful access to logs or data from intermediary services.
Prosecution and Legal Consequences
When law enforcement seizes servers from dark-net markets or illicit platforms, the data recovered often becomes critical in ongoing investigations. Servers can contain valuable evidence, such as user logs, transaction histories, encrypted communications, and wallet details, all of which assist in tracing activities to real-world identities. Even if investigations are slow or take years to develop, the information stored on seized servers can eventually provide new leads and actionable evidence. This data can be useless to law enforcement if encryption has been used for all communications.
Financial tracing and post-seizure analysis are key components of modern prosecution efforts. Law enforcement agencies use these methods to track cryptocurrency flows, identify individuals involved in specific transactions, and uncover hidden networks. This highlights the complexity of maintaining anonymity in dark-net environments, where any lapses in security can expose users to identification through recovered data. Privacy coins and their proper use remain essential to safeguarding transactions on the dark-net.
Conclusion
Dark-net markets leverage technologies like Tor, privacy coins, and encryption to provide anonymity and security, which can be essential for privacy-conscious users, including journalists, activists, and those in oppressive regimes. While these tools can be misused, they also protect individual freedoms. Despite strong security measures, vulnerabilities still exist, which can expose users to risks. The ongoing back-and-forth between dark-net operators and law enforcement reflects the complex balance between privacy, security, and accountability in the digital age. The dark-net, in its entirety, continues to raise important discussions about privacy and the ethical use of technology.
























0 Comments